If it`s not secure,
it`s not usable
As the industry is increasingly using information technology to achieve reduced use of resource by making process plants and machineries more transparent and accessible, the subject of security is becoming increasingly important. Secure data and information exchange between devices and services, has become one of the most important elements using the opportunies of Industrial Internet of Things.
As the industry is increasingly using information technology to achieve reduced use of resource by making process plants and machineries more transparent and accessible, the subject of security is becoming increasingly important. Secure data and information exchange between devices and services, has become one of the most important elements using the opportunies of Industrial Internet of Things.
A security model is an architecture that allows developers, administrators and end users to use applications in distributed environment while ensuring that the applications, the computers they run on and the information exchanged is not compromised. A complete security model has several facets including application security, transport security, user authorization and authentication and traceability. This understanding is the basis for OPC UA security.
A trustworthy, secure handling of sensitive data such as product and production knowledge is just as necessary as the protection against attacks on the networked systems. In order to counteract potential damage, Information Technology (IT) security should be ensured throughout the development process of a system and its software, from the requirements phase all the way to the decommissioning of the system.
Considerable security built into both atvise® and OPC UA
atvise® use safety standards as https to secure access. it also provides the ability to manage roles.
To further increase the level of security, there is a direct link to the security features available in OPC UA:
- Confidentiality: Data encryption against espionage and piracy
- Integrity: Data integrity to assure consistency
- Application Authentication: Application authentication, data transmitter and data users know each other.
- User Authentication: User authentication, to allow only permitted actions for a specific user
- User Authorization: Application authentication, data transmitter and data users know each other
- Auditing: Recording security-related events
- Availability: Availability of the system
The mechanisms of OPC UA user level security grant access for a specific user and its role while setting up a new session. OPC UA application level security is also part of the communication session and includes the exchange of digitally signed X.509 certificates.
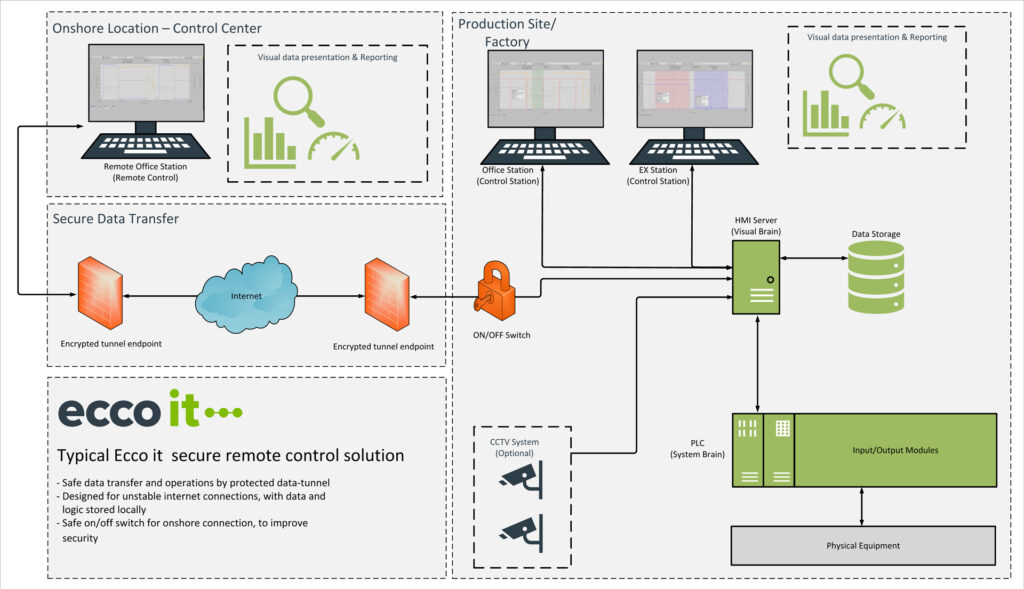
OUR SOLUTION FOR SECURE DATA TRANSFER
To ensure a fully secure data transfer between offshore and onshore locations, all communications pass through an encrypted tunnel. As an additional measure, the site network can be fully disconnected from the internet with a key switch, ensuring access only when explicitly granted. The system is designed to work with unstable and low-bandwidth links, with data and logic buffered locally to ensure operations do not break when the connection does.